Capture IP Addresses On Telegram Calls: Expert Wireshark Guide
In today’s digital communication landscape, privacy is a top concern. However, there are instances where identifying the IP address of someone you’re communicating with can be useful, especially during a Telegram call. One tool that helps achieve this is Wireshark, a powerful network protocol analyzer. In this guide, we will explore how to use Wireshark to capture network packets during a Telegram call and extract the other party’s IP address. We will cover the technical process, the underlying principles, and the ethical considerations involved.
Understanding Wireshark
Wireshark is an open-source packet analysis tool that allows users to capture and analyze the data traffic flowing through their network. Whether troubleshooting network issues, analyzing protocols, or identifying security threats, Wireshark provides a clear view of what is happening on a network. With its powerful features and user-friendly interface, it’s a must-have tool for cybersecurity professionals, network engineers, and tech enthusiasts alike.
Step-by-Step Guide to Capturing IP Addresses Using Wireshark
Step 1: Downloading and Installing Wireshark
Before diving into packet capturing, you need to download and install Wireshark on your computer. Here’s how to do it:
- Visit the official Wireshark website.
- Select and download the version that is compatible with your operating system (Windows, macOS, or Linux).
- Follow the installation instructions provided on the website.
Once installed, launch Wireshark. You’ll be greeted by an interface showing the available network interfaces that can be used to capture traffic.
Step 2: Filtering STUN Traffic
Telegram uses the STUN (Session Traversal Utilities for NAT) protocol during calls, which helps determine the public IP addresses of devices involved. To focus on this protocol, follow these steps:
- Open Wireshark and start monitoring the network traffic.
- In the filter bar (located at the top), type STUN to filter only STUN-related traffic.
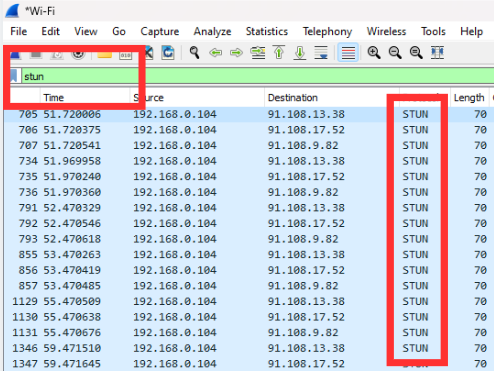
Alternatively, if you’re looking for more precision, use Wireshark’s search function:
- Click the search icon in the toolbar.
- Select the “String” option in the search settings.
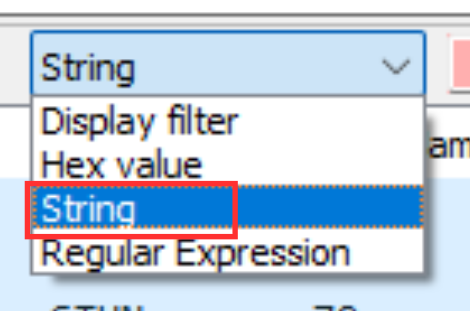
- In the search bar, type XOR-MAPPED-ADDRESS.
- Press Enter to start filtering for relevant traffic.
This string will specifically help you locate the IP address embedded in the STUN packets, as Telegram uses this protocol for communication during calls.
Step 3: Initiating Data Capture
With the filter set up, it’s time to capture the real-time network data while making a Telegram call.
- Make sure Wireshark is capturing data by pressing the green shark fin icon (or use
Ctrl + E). - Initiate a Telegram call with the user whose IP address you want to capture.

3. Once the call is answered, Wireshark will begin displaying network traffic related to the call, including STUN protocol packets.
As Wireshark captures traffic, it will show a stream of packets. Focus on the STUN-related packets, as they contain the IP address information.
Step 4: Identifying the IP Address
Now, it’s time to zero in on the specific IP address you’re looking for. To easily locate it:
- Use the search function again by clicking the Find option in Wireshark’s toolbar.
- In the search bar, type XOR-MAPPED-ADDRESS and press Enter.
- The user’s IP address will appear following the “XOR-MAPPED-ADDRESS” string in the packet details.
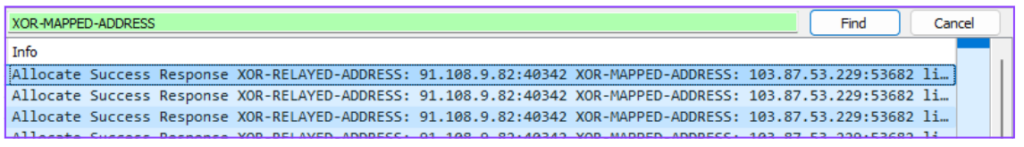
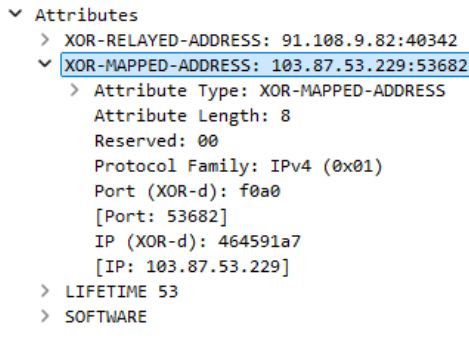
This IP address is the connection point for the user on the other end of the Telegram call.
Conclusion
By following these steps, you can effectively capture and analyze the IP address of someone you’re communicating with on Telegram using Wireshark. While the technical process is straightforward, always remember to adhere to privacy laws and ethical standards when conducting such activities.
If you’re passionate about delving deeper into cybercrime investigations and aspire to work with Law Enforcement Agencies, Cyber Cells, Police Departments, or become a Cyber Crime Consultant, consider enrolling in our Certified Cyber Criminologist (CCC) program. This exclusive live training is specifically designed for those who want to begin their careers as investigators. The CCC course offers premium modules covering real-world cybercrime scenarios, making it one of the most advanced programs in the field.







