Certified Enterprise Security Officer
Advanced Placement Driven Training Program
Enhance your corporate security expertise with our comprehensive course designed for entrepreneurs, business owners, and security analysts. Gain invaluable skills to safeguard small and medium-sized enterprises effectively.
Language: English & Hindi
*EMI Options Available

Program Overview
Certified Enterprise Security Officer is an advanced training program to excel in corporate securities and crack your first job in cybersecurity blue teaming domain. This course is well equipped with different tools and techniques corporate uses, multiple software usage and hands on learning through our labs.
This is entirely a Placement-Oriented program offering multiple job opportunities and wide range of experience over different licensed tools. This course has helped several students to crack their dream job in dream companies. Learn about Blockchain security, Kiosk Management, SOC and SIEM, Digital forensics, Smart contract exploitation, web application security, Honeypot setup and what not.
Top Skills you will learn
- 10+ Security Operations Centre Tools
- System Information Event Management
- 20+ Different industry job ready content
- Blockchain security and advanced exploitation
- Hand on experience over 15 licensed tools
Advanced Curriculum
An Advanced Curriculum with 21+ Industry ready topics. 100+ hours of live learning with 90% Hands on Practicals.
- Advanced IDS, IPS and Honeypot Setup
- DevSecOps with AWS, Azure and GCP
- ELK Stack, Wazuh SIEM, IBM Qradar
- Building Kiosk and Blockchain Security
- Web Application Security Attacks
Introduction to Blockchain
Smart Contracts Deployment
Non Fungible Tokens – NFT Scams
Digital Currency Security
Fundamentals of Splunk
Components & Architecture
Installation, Basic Use Cases
Importing Data in Splunk
Understanding KQL
Collecting Windows Logs in Splunk
Splunk Enterprise Security
Splunk Administrative Concepts
Changing Basic Options, License Management
Splunk App Installation
Index Bucket & Storage Calculation, User
Management,
Authentication Management, Data Ingestion
Forwarder, Indexer & Searched Config
Network Inputs
HTTP Event Collector
Fine Tuning
API Integration
Introduction to DevSecOps in AWS
Static Application Software Testing
Creating CI/CD Pipelines
Snyk and OWASP zap setup for DAST
Docker Container Securities
Cloud Security Posture Management
Installation of QRadar CE
QRadar Architecture DSM Install & Upgrade
Introduction to QRoC
Administrative Functions
Onboarding Linux As A Log Source in QRadar
Understanding Rules
Anomaly Detection Engine Rules and Building
Blocks & Applying Wincollect Patch
Wincollect Managed Onboarding and User
Creation
Windows Standalone Deployment and Sysmon
Integration
Custom Event Properties & Use Cases
…for a detailed syllabus description of 20+ modules ⬇️
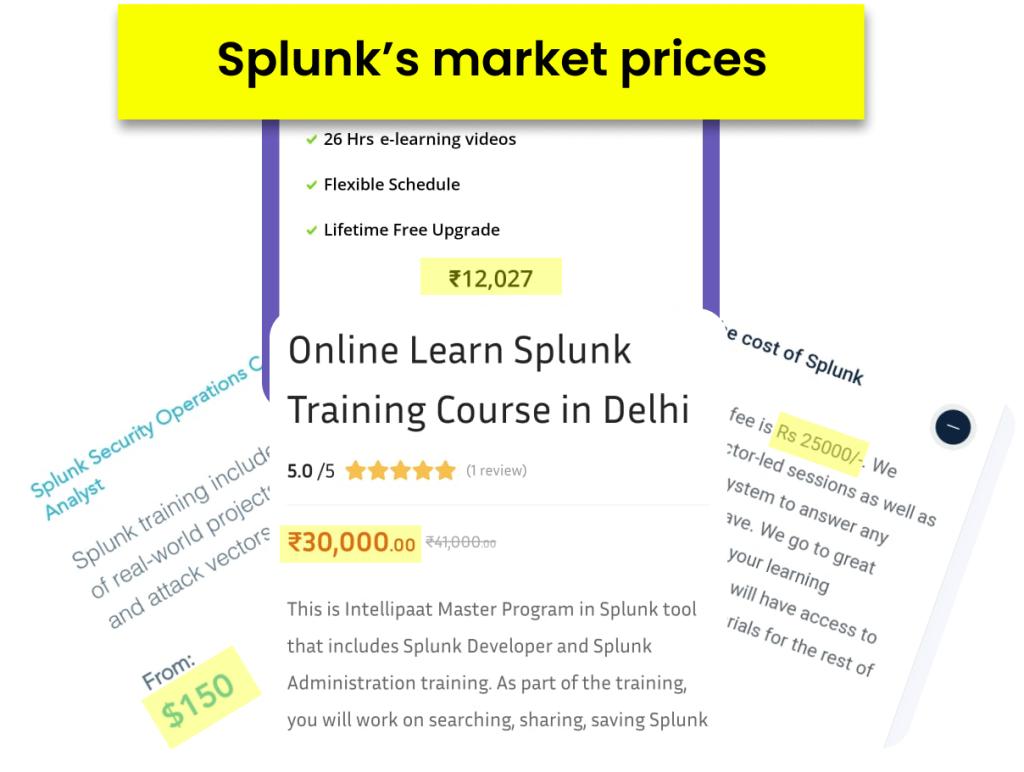
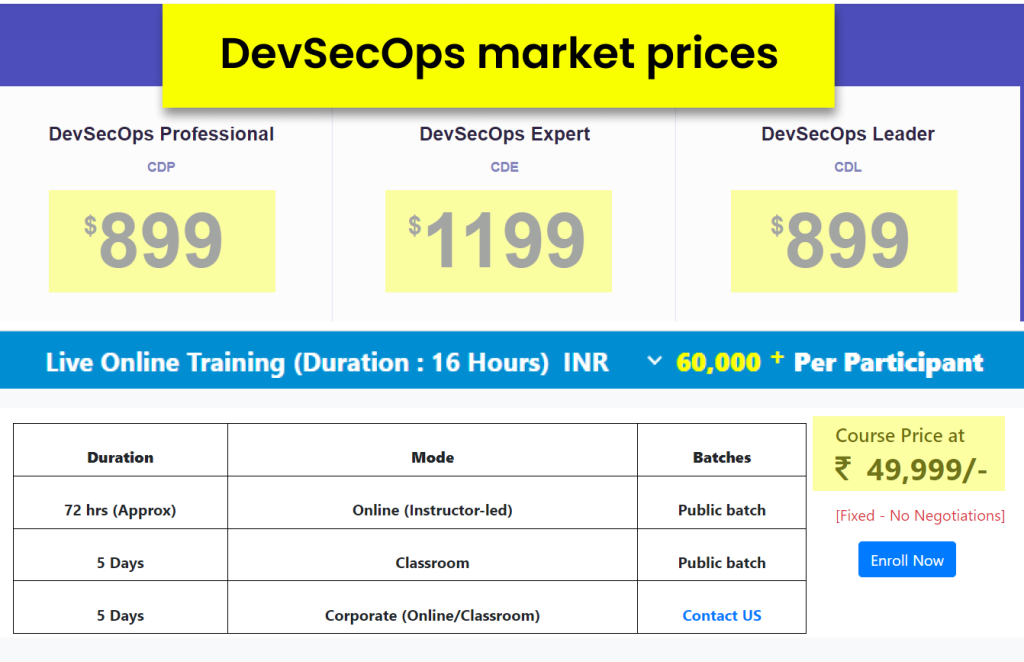
The industry rates are expensive! We've made it super-affordable for you.
Key Information
- Access to 120+ Labs and Practicals
- 100+ Hours of Live training
- Access to Notes and Recordings
- 24 X 7 Mentor Doubt Support
- Real time Industry Capstone Projects
Our Students Work At









