Clickjacking: The Invisible Threat Lurking Behind Clicks
Introduction
In the evolving world of cybersecurity, one of the more deceptive and visually undetectable threats is Clickjacking. This technique, often termed a UI Redress Attack, manipulates a user into performing actions they didn’t intend to. Whether it’s liking a social media post, subscribing to a newsletter, or transferring funds, clickjacking abuses the trust between users and websites.
In this blog, we’ll delve deep into what clickjacking is, how it works, different types of clickjacking attacks, real-world examples, and practical demonstrations you can try yourself.
What is Clickjacking?
Clickjacking is a user interface (UI) manipulation attack that tricks a user into clicking something different than what they perceive. In most cases, attackers embed legitimate website elements (like buttons or links) inside invisible iframes overlaid on a malicious website. When a victim interacts with the visible content, they are unknowingly interacting with the hidden content underneath.
How Clickjacking Works
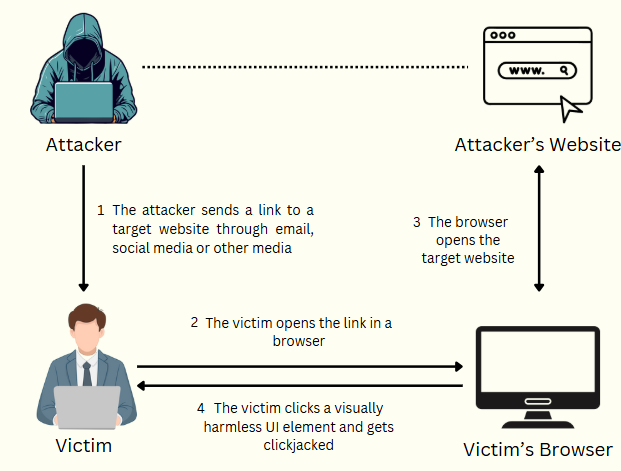
Here’s the core process behind a clickjacking attack:
- Legitimate Page: A trusted website has a critical button (like “Transfer Funds”).
- Malicious Page: An attacker hosts a page with enticing content (like a fake game, prize, or free download).
- Overlaying the Trusted Page: The attacker embeds the trusted page inside their page using an invisible iframe.
- Tricking the User: The attacker carefully aligns the critical button under some fake visual element (e.g., “Click to win $100”). When the user clicks, they actually trigger the real action (like transferring funds).
Why is Clickjacking Dangerous?
- Stealing money (banking portals).
- Hijacking social media accounts (likes, shares, follows).
- Changing security settings (disabling two-factor authentication).
- Subscribing users to premium services without consent.
Real-Life Clickjacking Examples
1. Facebook Clickjacking (2011)
A notorious case involved tricking users into liking Facebook pages they never saw. Malicious pages promised sensational content (like celebrity gossip). When users clicked “Play Video,” they unknowingly clicked an invisible “Like” button for a spam page.
2. Adobe Flash Settings Panel Attack
Flash Player’s security settings were embedded in many sites. Attackers found a way to frame this settings panel in invisible iframes, allowing them to remotely enable webcam and microphone access.
3. Twitter Clickjacking (2010)
A campaign tricked Twitter users into tweeting a spam message by placing an invisible “Tweet” button under a fake “Play” button.
Types of Clickjacking Attacks
1. Likejacking
- Specific to social media platforms.
- Tricks users into liking/sharing content without their consent.
2. Cursorjacking
- Replaces the actual cursor with a fake one, misaligning the visible and actual click targets.
- Used in phishing and fake login forms.
3. Filejacking
- Exploits drag-and-drop functionality.
- Tricks users into uploading files to malicious servers.
4. Formjacking
- Overlays legitimate forms (like login or payment forms) with fake ones to steal credentials.
Practical Demonstration – Clickjacking Lab
Objective: Create a Clickjacking PoC (Proof of Concept) to demonstrate how it works.
Tools Required:
- A basic web server (XAMPP, Python HTTP server, etc.)
- HTML & CSS knowledge
Step 1: Create a Victim Page (target.html)
This is the page the attacker wants to trick the user into interacting with.
<!DOCTYPE html>
<html>
<head>
<title>Victim Page</title>
</head>
<body>
<h1>Click to Transfer Funds</h1>
<button onclick="alert('Funds Transferred!')">Transfer Funds</button>
</body>
</html>Step 2: Create the Malicious Page (clickjack.html)
This page will embed the victim page using an invisible iframe.
<!DOCTYPE html>
<html>
<head>
<title>Clickjacking Demo</title>
<style>
iframe {
opacity: 0; /* Make iframe invisible */
position: absolute;
top: 50px;
left: 50px;
width: 200px;
height: 50px;
z-index: 2;
}
#fakeButton {
position: absolute;
top: 50px;
left: 50px;
width: 200px;
height: 50px;
background-color: lightblue;
z-index: 1;
cursor: pointer;
}
</style>
</head>
<body>
<h2>Click to Win an iPhone!</h2>
<div id="fakeButton">Click Here!</div>
<iframe src="http://localhost/target.html"></iframe>
</body>
</html>Step 3: Run the Demo
- Place both files inside your web server root directory.
- Visit
http://localhost/clickjack.htmlin your browser. - When the user clicks “Click Here!” they actually trigger the Transfer Funds button on the victim page.
Step 4: Explanation
- The
iframeembeds the victim page. - The victim page is invisible.
- The fake button visually tricks the user into thinking they are clicking something harmless.
- The click passes through to the real button underneath.
Advanced Practical – Social Media Likejacking
You can modify this technique to “auto-like” a page. For example:
- Embed
https://www.facebook.com/SomePagein an iframe. - Position the “Like” button directly under some fake clickable element.
- This abuses the same principle.
Preventing Clickjacking
1. X-Frame-Options Header
Set this HTTP header on your website:
X-Frame-Options: DENYThis blocks your page from being framed into another website.
2. Content Security Policy (CSP) Frame Ancestors
A stricter and modern approach:
Content-Security-Policy: frame-ancestors 'self'This allows only your own domain to frame your content.
3. Frame Busting Scripts (Client-Side)
Embed this script in your pages:
if (top != self) {
top.location = self.location;
}This forces your page to break out of any frame.
4. User Awareness
Educate users to avoid clicking on sensational links, unknown pop-ups, or suspicious buttons.
Modern Clickjacking – Beyond Simple Frames
Mobile App Clickjacking
- Overlays fake UI elements on top of banking apps.
- Tricks users into authorizing transactions.
AR/VR Clickjacking
- Virtual reality interfaces trick users into interacting with hidden content.
Conclusion
It may seem simple, but its impact can be devastating. It exploits the gap between what a user sees and what actually happens when they click. Even in 2025, variations of clickjacking are used in phishing campaigns, malvertising, and social media scams.
Don’t miss out! Check out our latest blogs for bug bounty hunters:






