Open Redirect Vulnerabilities: How To Prevent Attacks, Secure Your Website & Protect User Data in 2025
Introduction
Cybersecurity threats continue to evolve, and attackers consistently exploit weaknesses in web applications to compromise users and systems. One such vulnerability that remains prevalent is the Open Redirect Vulnerability. While it may appear harmless at first glance, this security flaw can be exploited for phishing attacks, malware distribution, and session hijacking.
This article explores the mechanics, risks, real-world examples, and mitigation strategies of Open Redirect vulnerabilities, helping developers and security professionals secure their web applications effectively.
Understanding Open Redirect Vulnerabilities
An Open Redirect Vulnerability occurs when an application blindly redirects users to a URL specified in an unvalidated input parameter. This means an attacker can craft a malicious link that redirects users to phishing sites, malware-infected pages, or other dangerous destinations.
For example, consider a legitimate website that allows redirection via a URL parameter:
https://example.com/redirect?url=https://legitimate-site.comAn attacker could modify this to:
https://example.com/redirect?url=https://malicious-site.comIf the application does not properly validate or restrict the target URL, it will redirect users to the malicious site, potentially leading to credential theft or malware infections.
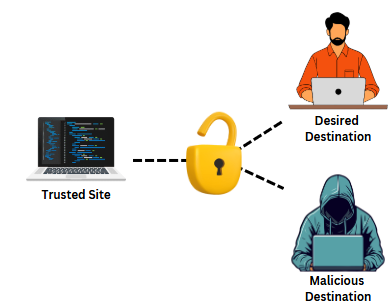
How Open Redirect Attacks Work
Step 1: Identifying an Open Redirect Vulnerability
Attackers look for parameters such as url=, redirect=, next=, or returnUrl= that accept arbitrary external URLs without validation. These parameters are often used in login flows, payment gateways, or URL-shortening services.
Step 2: Crafting a Malicious URL
Once a vulnerable endpoint is found, an attacker crafts a deceptive URL containing a redirection to a malicious website. For example:
https://example.com/redirect?url=https://malicious-site.comStep 3: Social Engineering and Phishing
The attacker distributes this URL via emails, social media, or instant messaging, tricking users into believing it leads to a trusted destination. Since the link starts with example.com, users may not realize they will be redirected to a phishing or malware-laden website.
Step 4: Exploiting the User
Once users are redirected, attackers can:
- Steal credentials via fake login pages.
- Install malware by prompting users to download infected files.
- Conduct session hijacking by stealing authentication tokens or session cookies.
Real-World Examples of Open Redirect Exploits
1. Google Open Redirect Abuse
In the past, Google’s URL redirection service (www.google.com/url) was exploited by attackers to create seemingly legitimate phishing links. Users trusted the google.com domain, unaware that they were being redirected to a fake login page that stole their credentials.
2. PayPal Phishing Attacks
Cybercriminals leveraged an Open Redirect vulnerability in PayPal’s login flow to trick users into entering their credentials on fraudulent sites. Because the URL contained paypal.com, victims assumed the link was safe.
3. Social Media Scams
Scammers exploited Open Redirect vulnerabilities in Facebook, Twitter, and LinkedIn to distribute spam and malicious advertisements, bypassing content filtering and deceiving users into clicking harmful links.
Risks Associated with Open Redirect Vulnerabilities
1. Phishing Attacks
Open Redirects allow attackers to create phishing links that appear legitimate. Since users trust the base domain, they may unknowingly enter sensitive information on fake login pages.
2. Malware Distribution
Cybercriminals use Open Redirects to deliver malware by redirecting users to compromised sites that exploit browser vulnerabilities and download malicious payloads.
3. Reputation Damage
If a website is known to facilitate Open Redirect attacks, it can be blacklisted by security firms and browsers, damaging its reputation and credibility.
4. Session Hijacking and Token Theft
Attackers can use Open Redirects to steal session cookies or authentication tokens, allowing them to hijack user accounts without requiring passwords.
How to Detect Open Redirect Vulnerabilities
1. Manual Testing
- Identify URLs that accept redirection parameters (
?redirect=,?url=,?next=). - Test with arbitrary external URLs and observe if the application redirects without validation.
- Try obfuscating malicious URLs using encoding techniques (e.g.,
base64, URL encoding).
2. Automated Scanning
- Use tools like Burp Suite, OWASP ZAP, or Nmap scripts to detect Open Redirect issues in web applications.
- Deploy Web Application Firewalls (WAFs) with security rules to log and block suspicious redirects.
3. Reviewing Source Code
- Check if user-supplied input for redirections is properly validated.
- Ensure the application does not use user-controlled input for constructing redirect URLs without verification.
How to Prevent Open Redirect Vulnerabilities
1. Allow Only Internal Redirects
Restrict redirects to trusted domains within your application:
# Example in Python Flask
from flask import request, redirect, abort
ALLOWED_DOMAINS = ["example.com"]
def is_safe_redirect_url(target_url):
from urllib.parse import urlparse
parsed_url = urlparse(target_url)
return parsed_url.netloc in ALLOWED_DOMAINS
@app.route('/redirect')
def safe_redirect():
url = request.args.get('url')
if not url or not is_safe_redirect_url(url):
abort(400) # Bad Request
return redirect(url)2. Use Relative URLs Instead of Absolute URLs
If possible, only allow redirections within your domain:
https://example.com/redirect?path=/dashboardThis ensures users remain within the trusted site.
3. Validate and Sanitize Input
- Use whitelists to allow only predefined URLs.
- Reject full URLs containing
http://orhttps://unless necessary. - Normalize URLs to prevent encoding tricks used in attacks.
4. Display a Warning Before Redirecting
Show users a confirmation page before redirecting them:
You are about to leave example.com and visit [malicious-site.com].
Do you want to proceed? Yes | No5. Monitor and Log Redirect Activities
- Keep track of all redirects using server-side logging.
- Set up alerts for unusual redirection patterns.
- Regularly review logs to detect abuse.
Conclusion
Open Redirect vulnerabilities may seem minor but can be weaponized for phishing, malware distribution, and account takeovers. Developers must take proactive steps to prevent unvalidated redirects by restricting user input, validating URLs, and implementing security best practices.
By staying vigilant, conducting regular security assessments, and following the mitigation strategies outlined above, organizations can significantly reduce the risks associated with Open Redirect vulnerabilities.
Key Takeaways
✔ Open Redirects can be exploited for phishing and malware attacks. ✔ Validate and sanitize all user-controlled redirect URLs. ✔ Restrict redirections to trusted domains or use relative paths. ✔ Display warnings before redirecting users. ✔ Monitor and log all redirection activities for suspicious behavior.
Understanding and addressing Open Redirect vulnerabilities is crucial in fortifying web applications against cyber threats. Stay secure and keep learning!
Don’t miss out! Check out our latest blogs for bug bounty hunters:






