Understanding the Digital Forensics Investigation Process
In the digital age, where our lives are increasingly intertwined with technology, the field of digital forensics stands as a crucial pillar in uncovering digital evidence, solving cybercrimes, and ensuring justice. This article aims to explore the intricacies of digital forensics investigation, from its foundational principles to its practical applications and challenges in today’s evolving landscape of cyber threats.
Introduction to Digital Forensics
Digital forensics, also known as computer forensics, is the process of methodically examining and analysing digital devices and digital data to uncover evidence that can be used in legal proceedings. It involves the application of forensic techniques to recover, preserve, and examine data from computers, mobile devices, networks, and other forms of digital storage.
Key Principles and Processes
Digital forensics investigations typically follow a structured process to ensure the integrity and admissibility of evidence:
- Identification and Collection: The first step involves identifying potential sources of digital evidence collection. This could include seizing computers, smartphones, servers, or even cloud storage accounts that may contain relevant information.
- Preservation: Once identified, digital evidence must be carefully preserved to maintain its integrity and reliability. Forensic specialists use specialised tools and techniques to create forensic copies of data, ensuring that the original evidence remains unchanged.
- Analysis: In the analysis phase, forensic examiners meticulously examine the preserved data to extract relevant information. This may involve recovering deleted files, examining internet browsing history, decrypting encrypted data, and reconstructing digital communications.
- Interpretation and Reporting: After analysis, findings are interpreted and documented in a detailed report. This report outlines the methods used, the evidence collected, and the conclusions drawn from the analysis. Clear and concise reporting is essential for presenting findings in court or other legal proceedings.
Applications of Digital Forensics
Digital forensics finds application across various domains, including law enforcement, corporate investigations, cybersecurity incident response, and legal proceedings. Some key applications include:
- Cybercrime Investigations: Digital forensics plays a crucial role in investigating cybercrimes such as hacking, data breaches, online fraud, and cyber espionage. Forensic examiners analyse digital evidence to identify perpetrators, track their activities, and establish a chain of custody for evidence.
- Corporate Investigations: In the corporate world, digital forensics is used to investigate employee misconduct, intellectual property theft, insider threats, and regulatory compliance violations. It helps organisations protect their sensitive information and maintain data integrity.
- Incident Response: During cybersecurity incidents, digital forensics helps organisations understand the nature and scope of the breach, identify compromised systems, and mitigate further damage. Rapid response and forensic analysis are critical to minimising the impact of cyber incidents.
Challenges in Digital Forensics
Despite its importance, digital forensics faces several challenges in today’s digital landscape. The below mentioned keywords elaborate how digital forensic works in these challenges:
- Encryption: The widespread use of encryption poses challenges for forensic examiners trying to access and analyse encrypted data. Techniques such as cryptographic analysis and brute-force attacks may be employed to decrypt protected information.
- Volume and Variety of Data: The sheer volume and diversity of digital data generated by modern devices can overwhelm forensic investigators. Advanced tools and techniques are required to efficiently process, filter, and analyse large datasets.
- Legal and Ethical Considerations: Digital forensics must adhere to strict legal and ethical guidelines to ensure the admissibility of evidence in court. Privacy concerns, chain of custody issues, and jurisdictional challenges often complicate forensic investigations.
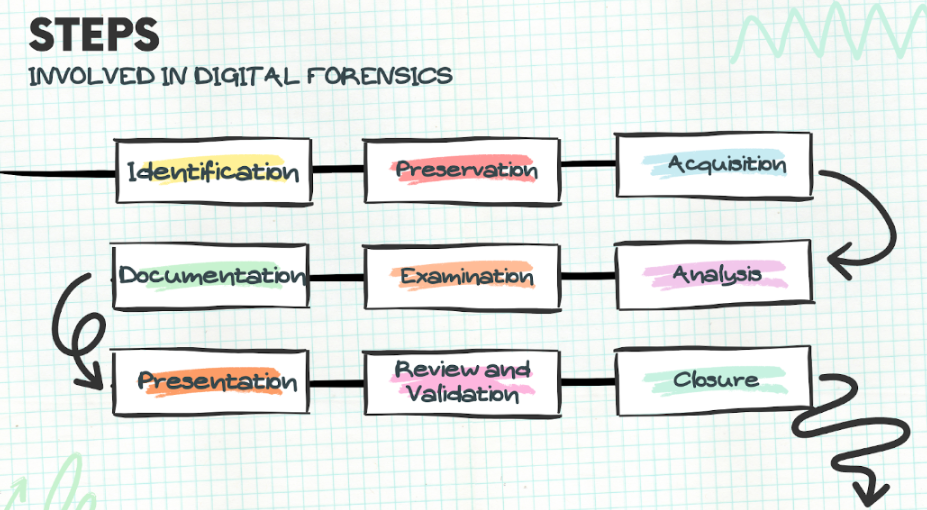
Steps Involved In Digital Forensic
Digital forensic investigation is a structured process aimed at uncovering digital evidence that can be used in legal proceedings. The steps involved digital forensic investigation can be outlined as follows:
- Identification:
- Scope Definition: Define the scope of the investigation based on the incident or allegations. Determine which devices, systems, or digital assets need to be examined.
- Evidence Identification: Identify potential sources of digital evidence, such as computers, smartphones, servers, cloud accounts, and network logs.
- Preservation:
- Evidence Collection: Collect physical devices or create forensic images of digital evidence using write-blocking techniques to prevent alteration of data.
- Chain of Custody: Document the chain of custody to ensure the integrity and admissibility of evidence in court.
- Acquisition:
- Forensic Imaging: Create forensic images of storage devices using specialised tools and techniques. This ensures a bit-by-bit copy of the original data, preserving its integrity.
- Analysis:
- Data Recovery: Use forensic software and techniques to recover deleted, hidden, or encrypted data from the forensic images.
- Keyword Searches: Conduct keyword searches to identify relevant files, documents, communications, or metadata.
- Timeline Reconstruction: Piece together a timeline of events based on recovered data to understand the sequence of activities.
- Link Analysis: Analyse relationships and connections between individuals, devices, or entities involved in the case.
- Examination:
- Forensic Examination: Analyze recovered data to identify artefacts that are relevant to the investigation, such as documents, emails, chat logs, images, and timestamps.
- Hash Analysis: Calculate hashes of files and compare them with known hashes to verify integrity and detect alterations.
- Documentation:
- Report Generation: Document findings, methods used, and analysis results in a detailed forensic report. Include metadata, timestamps, and other relevant information.
- Legal Compliance: Ensure that the investigation adheres to legal requirements and standards for the admissibility of digital evidence in court.
- Presentation:
- Expert Testimony: Present findings and conclusions as expert testimony in legal proceedings. Explain technical aspects clearly to stakeholders, including judges, juries, and lawyers.
- Review and Validation:
- Quality Assurance: Conduct peer reviews or quality checks to validate findings and ensure accuracy in the forensic report.
- Validation of Methods: Ensure that forensic methods used are scientifically sound and follow established best practices.
- Closure:
- Case Closure: Conclude the investigation by securely storing evidence and maintaining documentation for potential future reference or legal challenges.
- Lessons Learned: Review the investigation process to identify areas for improvement or lessons learned that can enhance future investigations.
Emerging Trends and Technologies
Advancements in technology continue to shape the field of digital forensics:
- Machine Learning and AI: Machine learning algorithms are increasingly used to automate the analysis of large datasets, identify patterns, and detect anomalies in digital evidence.
- Blockchain Forensics: With the rise of cryptocurrencies and blockchain technology, forensic experts are developing techniques to trace transactions and uncover illicit activities conducted using blockchain platforms.
- Cloud Forensics: As more data migrates to cloud services, cloud forensics has emerged as a specialised area within digital forensics. Investigators must adapt to the unique challenges posed by remote data storage and virtualized environments.
Conclusion
In conclusion, digital forensics is a dynamic and essential discipline that plays a critical role in investigating cybercrimes, ensuring data integrity, and upholding justice in the digital age. By following rigorous methodologies and leveraging advanced technologies, forensic investigators uncover digital evidence that can be instrumental in legal proceedings and cybersecurity operations. As technology continues to evolve, so too must the practices and techniques employed in digital forensics to effectively address emerging cyber threats and protect digital information.
Read more blogs on cybersecurity
The Impact of Cryptocurrency on Cybercrime – Virtual Cyber Labs






